BlueKeyVault
The "On premise" Key Vault
Safeguarding Your Digital Assets
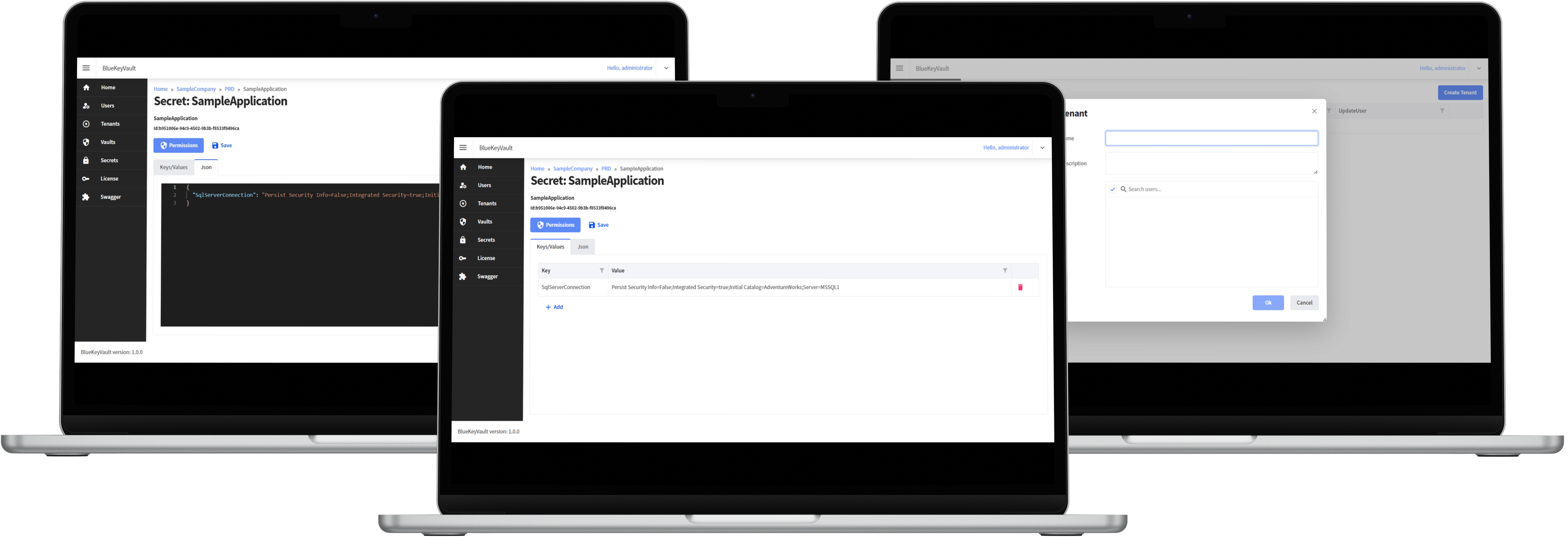
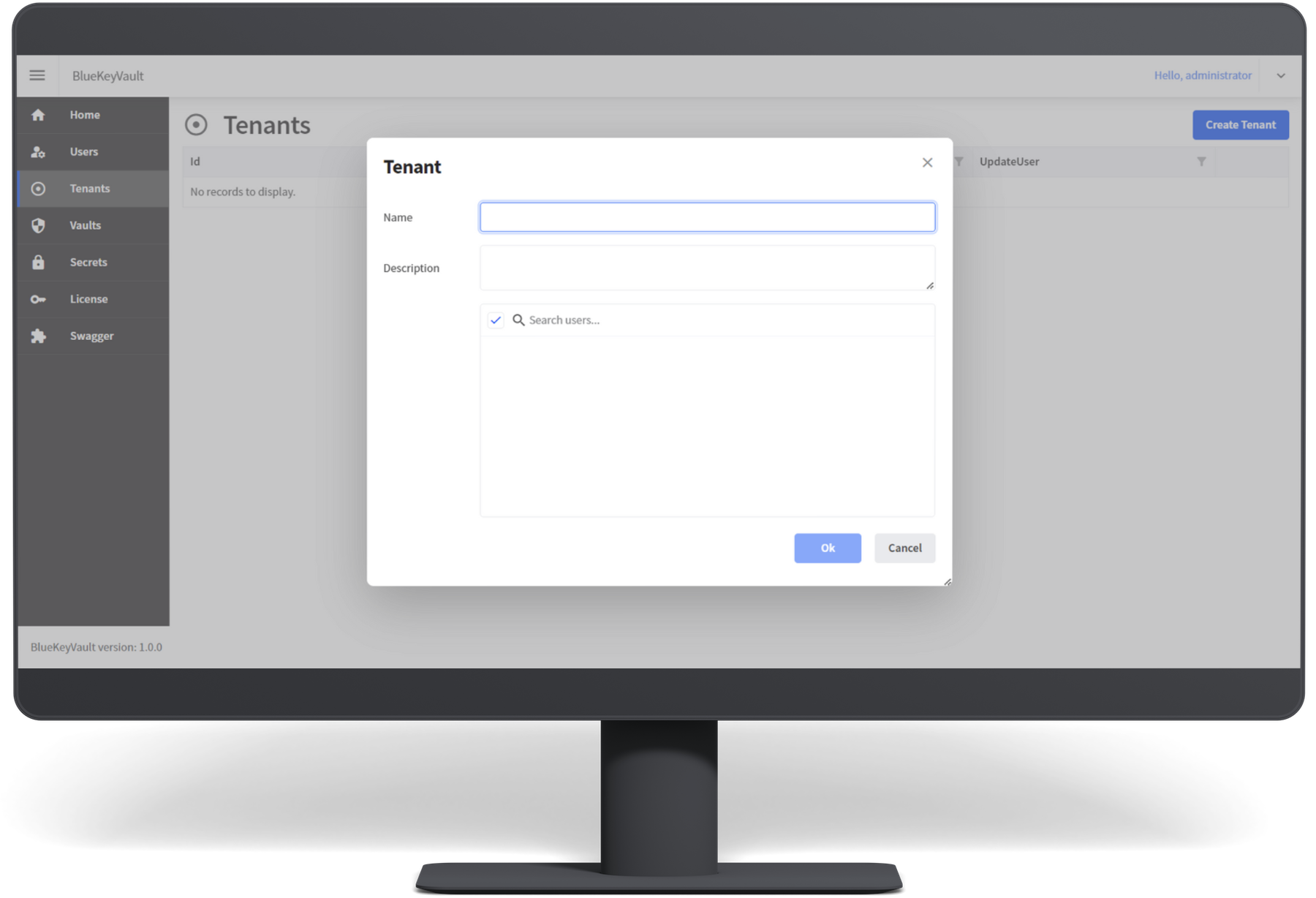
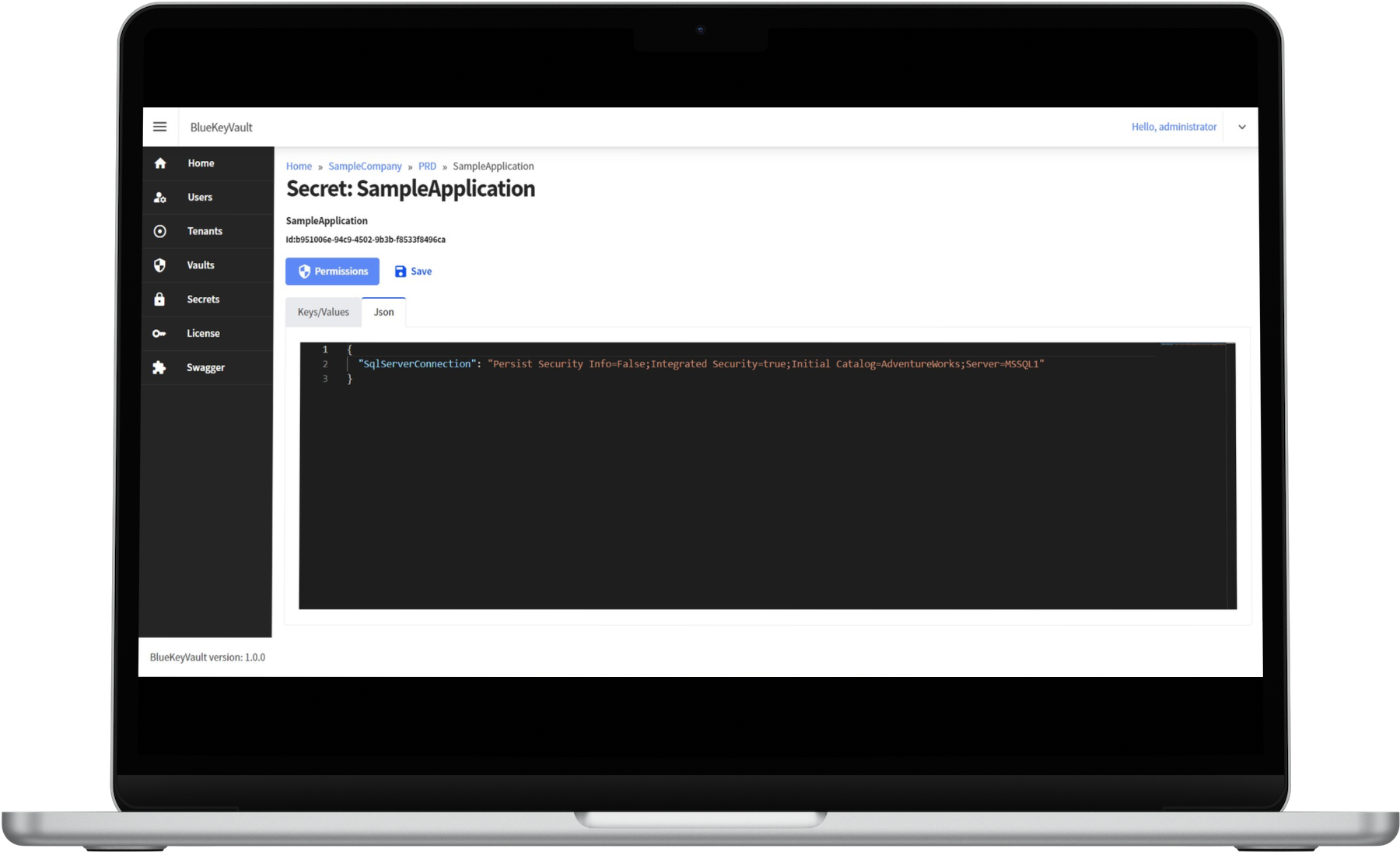
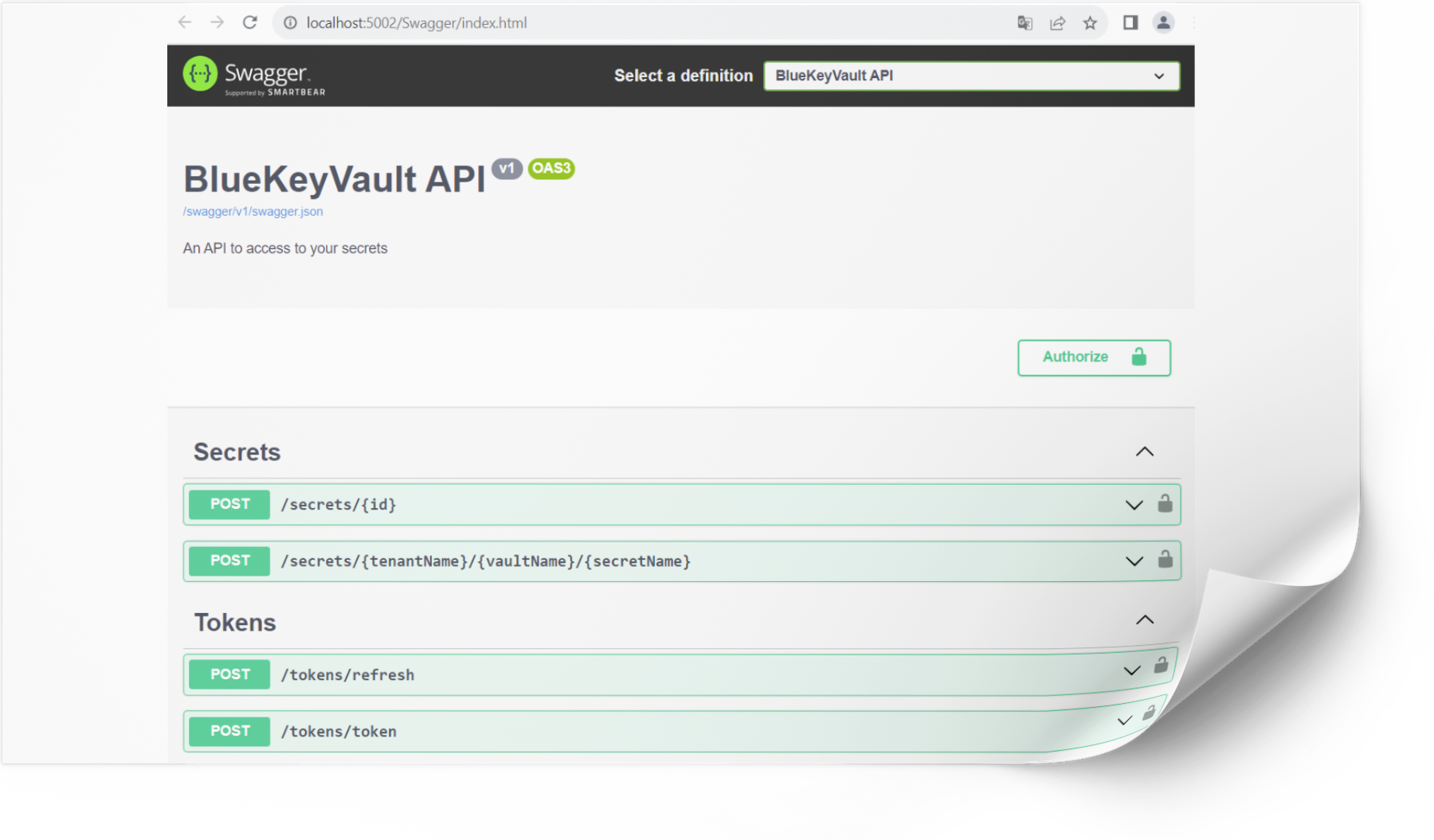
At BlueKeyVault, we understand the paramount importance of securing your sensitive information and digital assets. Our state-of-the-art key vault solutions provide a robust and reliable platform to protect your credentials, cryptographic keys, passwords, and other confidential data without exposing them in the configuration files
Download Now